Over 40,000+ businesses trust us to streamline their cloud security operations with an industry-leading platform

Gain clear, prioritized insights into all cloud resources, from development through production.
Use the user-friendly interface to apply least-privilege policies without slowing down workflows.
Avoid last-minute audit stress. Continuously monitor, validate, and generate compliance reports automatically.

Explore the eBook to uncover:

Achieve comprehensive oversight across AWS, Azure, GCP, and Oracle Cloud Infrastructure (OCI) through completely agentless scanning. Automatically map your cloud ecosystem including infrastructure, workloads, user access, and information assets with powerful visualization capabilities. Access a centralized dashboard that helps your team quickly grasp even the most intricate security challenges.
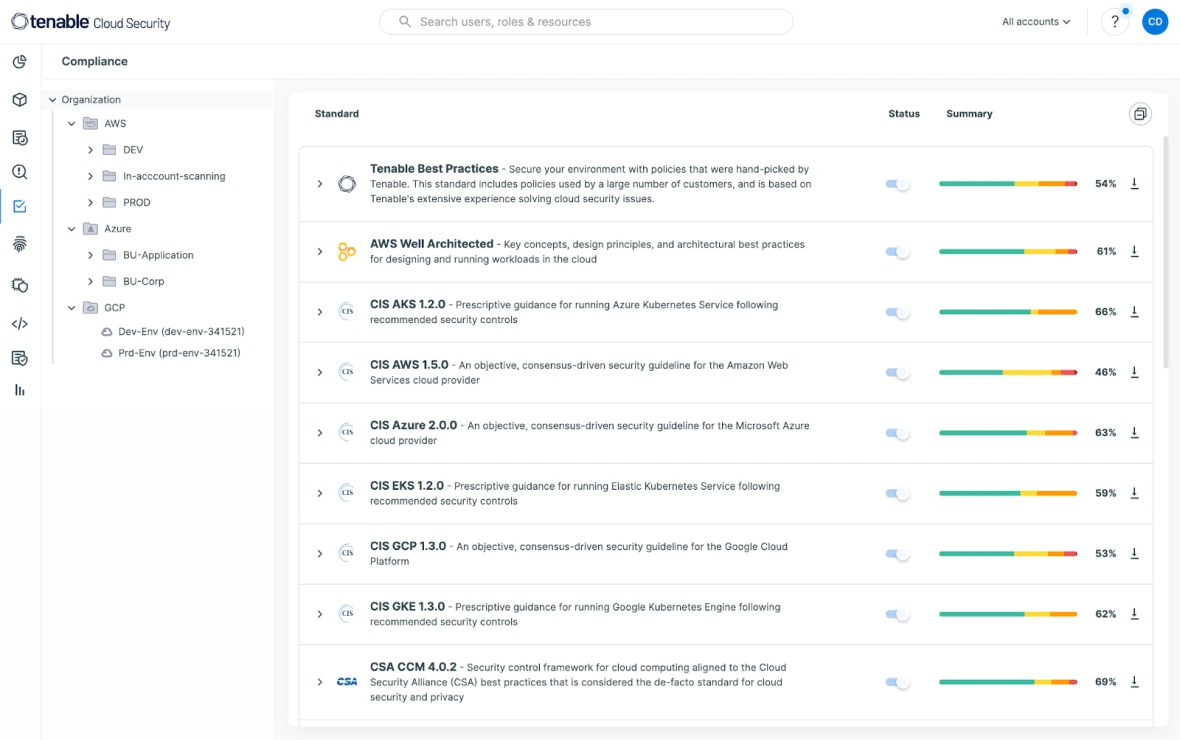
Try for freeTrack security threats through ongoing evaluation of cloud infrastructure settings and configurations. Align identified vulnerabilities with industry standards and internal policies to achieve lasting compliance and streamline audit processes across all cloud platforms. Leverage ready-made compliance reports for over 20 frameworks including SOC-2, GDPR, PCI DSS, HIPAA, NYDFS, and more.
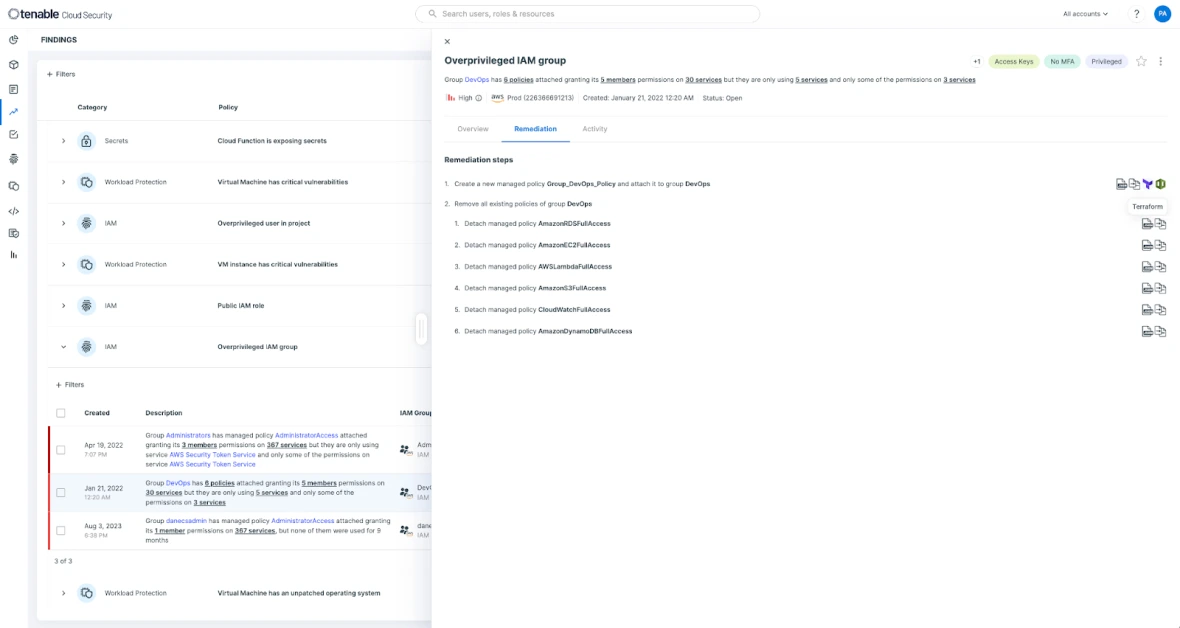
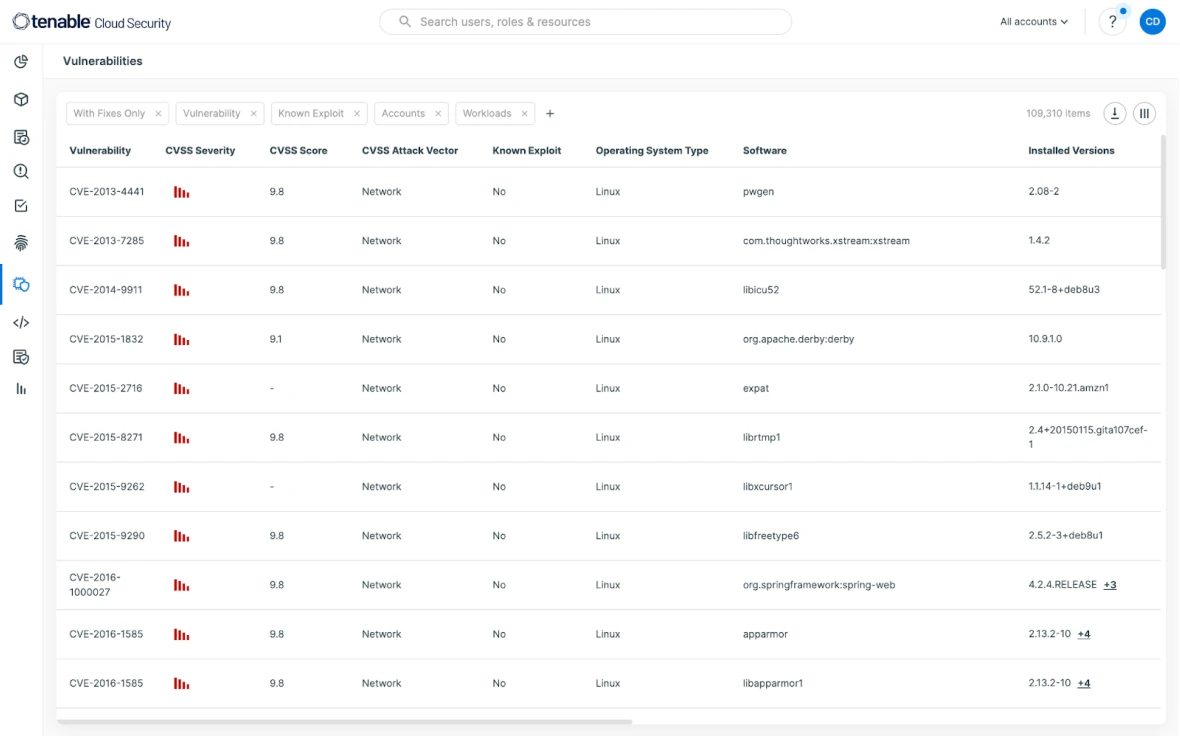
Try for freeVeximbo delivers a cloud security platform that enables you to concentrate on the most critical vulnerabilities. Our solution provides intelligently ranked security insights that enable Security and DevSecOps professionals to streamline threat identification and resolution at enterprise scale. Address dangerous permissions and configuration errors through automated and adaptable policies that integrate effortlessly with ticketing systems, CI/CD workflows, Infrastructure as Code, and existing processes.
Try for freeIdentify unusual and potentially malicious behavior through constant comparison against established activity patterns. Process cloud platform logs and correlate security threats with your infrastructure to rapidly reveal the full context surrounding each vulnerability.
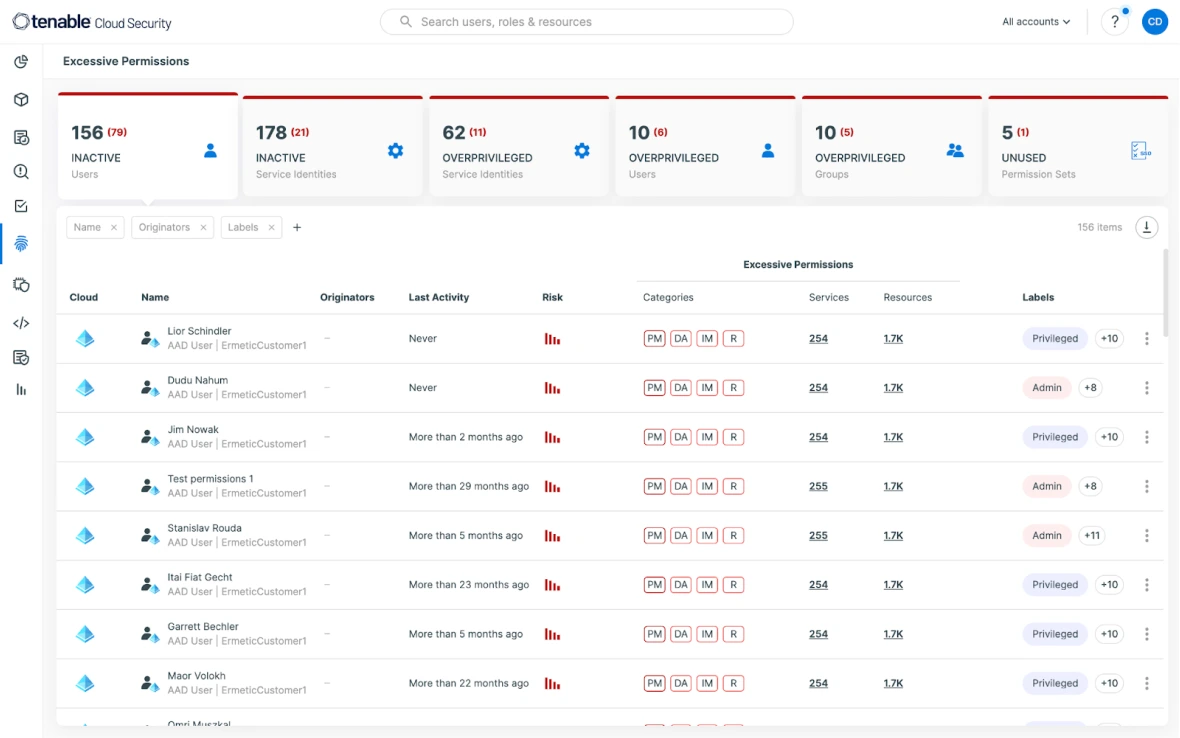
Try for freeEstablish a zero-trust framework within your cloud infrastructure. Reduce unnecessary access rights for both applications and users while maintaining operational continuity. Achieving least privilege begins with comprehensive visibility into all access entitlements. Automatically identify all users and authorization policies (encompassing IAM, resource permissions, boundaries, and access control lists) and examine their connections to uncover discrepancies between your intended security posture and current permission grants.
Try for free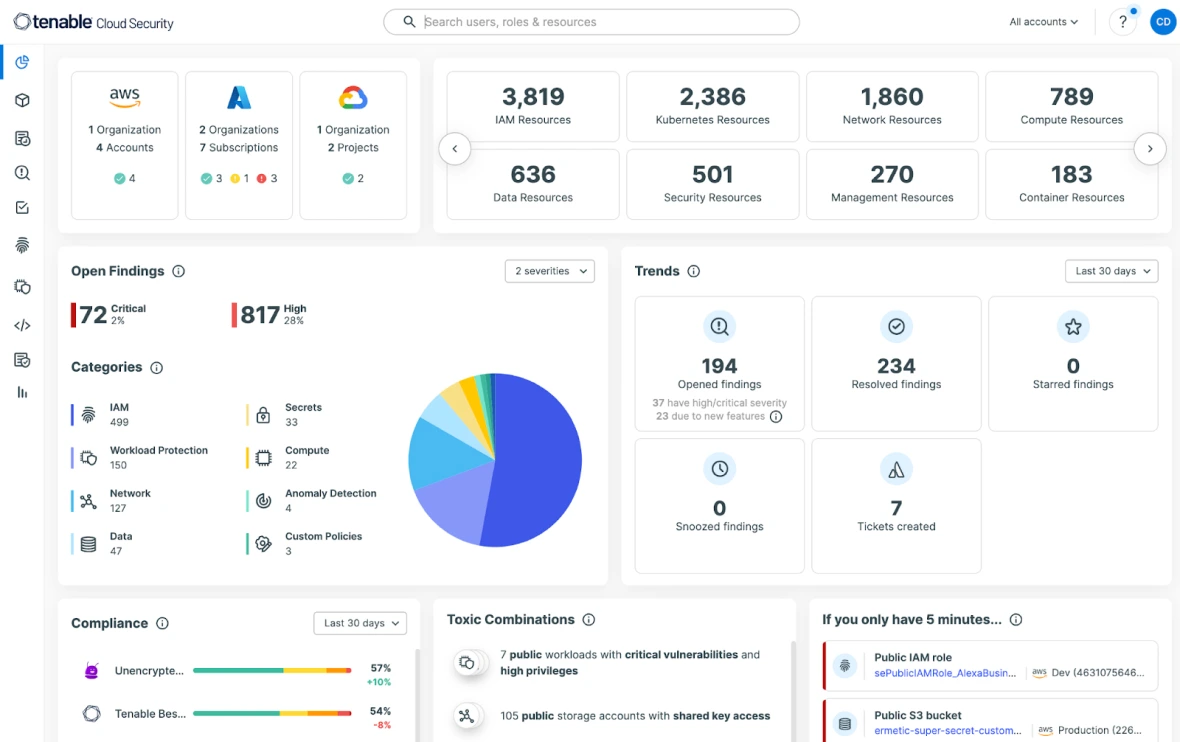

Outstanding integrated cloud protection is within reach!
We'll demonstrate precisely how Veximbo Cloud Security enables you to achieve comprehensive multi-cloud resource visibility, intelligent risk ranking, and streamlined compliance reporting.